TT® FIX Order Routing
Configuring client connectivity
UAT FIX client connectivity is available via the Internet or Stunnel (secure Internet).
TT supports SSL-wrapped TCP connections for FIX connections. TT encrypted FIX utilizes server-side certificates only, similar to how most Secure HTTP (https) websites are implemented. Client certificates are not utilized or checked; client authentication occurs at the FIX protocol level utilizing SenderCompID in FIX tag 49 and password in FIX tag 96.
If your FIX engine natively supports SSL encryption, please consult the documentation for your FIX engine for configuration details. TT provides the stunnel.zip file which contains the TTFIX.crt. This file contains the public certificates utilized by the TT Platform's FIX endpoints for customers’ use to minimize the risk of a Man-in-the-Middle attack.
If your FIX engine does not natively support SSL encryption, TT recommends using the open source stunnel proxy to implement the SSL encryption wrapper. Stunnel is available from https://www.stunnel.org/ and supports multiple operating systems, including Linux and Windows. Stunnel encrypts only the individual FIX connection, rather than implementing a full VPN tunnel as was traditionally used to encrypt FIX.
Your company on-premises DNS services must be able to access public DNS entries below pending the connection method:
| Internet | Stunnel | |
|---|---|---|
| FIX Order Routing | fixorderrouting-ext-uat-cert.trade.tt: 11502 | fixorderrouting-ext-uat-cert.trade.tt: 11702 |
To configure connections for stunnel:
-
Install the
stunnel software, if
necessary.
Note: The first time you install stunnel, you might receive
a prompt similar to the following. If so, simply enter the appropriate
information for your location and organization.
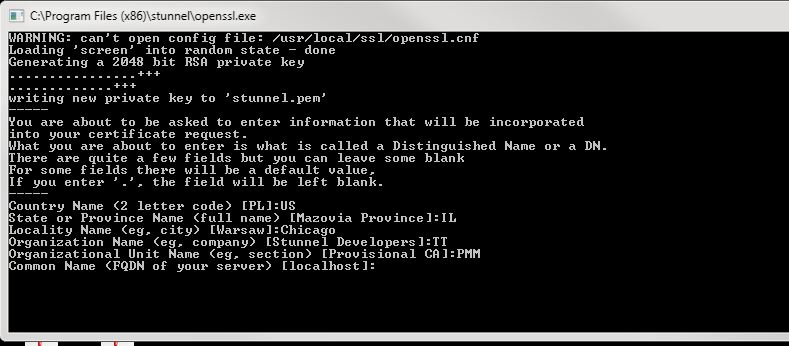
- Download TT's stunnel.zip file. The zip file contains the TTFIX.crt public cert file and a sample stunnel client configuration file.
- Copy the TTFIX.crt file to the appropriate location on your system.
-
Add the following to the stunnel configuration:
[orfix-tcp]where FullyQualifiedDomainName:port uses one of the values from the table above. FIX clients should use the following connection information:
client = yes
accept = 127.0.0.1:11702
connect = FullyQualifiedDomainName:port
CAfile = TTFIX.crt
verify = 3
- Host: 127.0.0.1
- Port: 11702