Risk Administration
Data File Uploads
Overview
Note: Firefox does not support the Data Uploads or Auto Uploads feature. Please use another browser to access these features.
The Data Uploads and Auto Uploads pages provide you with an interface for manually or automatically uploading data files directly into the Setup database for users in your company:
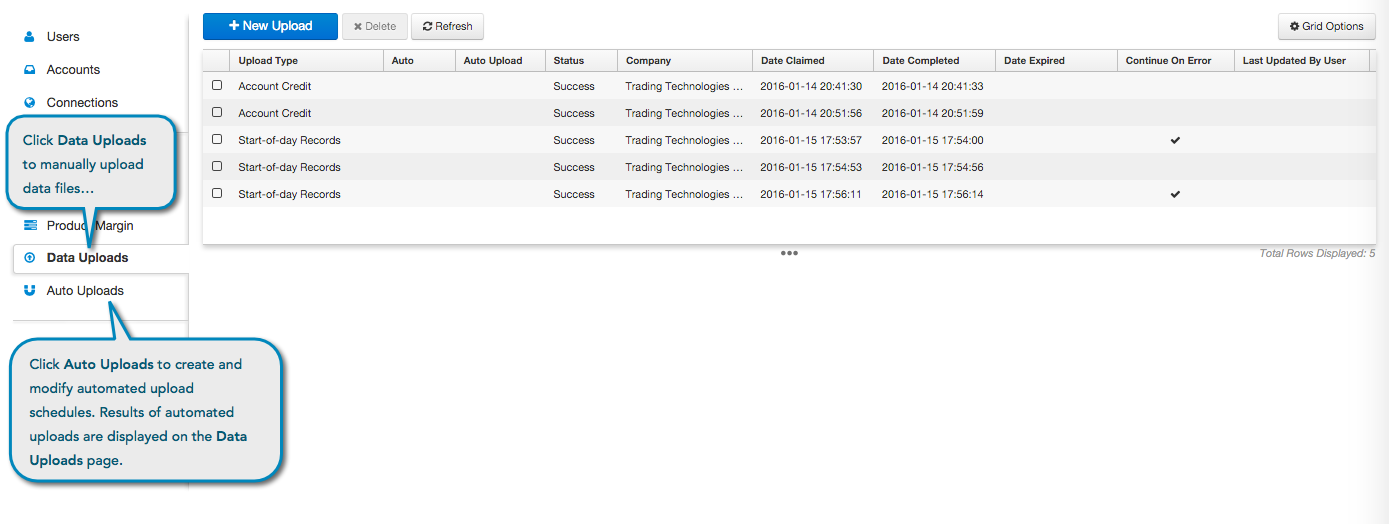
Auto Uploads
As a company administrator, use the Auto Uploads page to create automated upload schedules for credit, margin, and SOD files. You can also use the Data Uploads page to manually upload the same files:
- Credit
- Start of Day
- Product Margin
- Trayport Market Activity File/Generic Audit Trail File (TT Score)
Configuring Access for File Uploads
File Uploads via Public Internet
Your administrator may wish to configure TT access to retrieve files by allowing the requests to come from registered TT IP addresses. However, these IP addresses are dynamically issued and may change without notice. To help identify the valid IP addresses, TT has created the ttuploader.trade.tt URL.
Administrators can perform a name server lookup (nslookup) on the DNS entry for the ttuploader.trade.tt URL and receive the list of the most recently allocated IP addresses for risk file uploads. Once requested, the service returns a list of all the possible sources that TT traffic may originate for that specific task.
To retreive a list of valid IP addresses for risk file uploads:
Open a Terminal or Command-Line window.
Enter the following command to perform the nslookup for ttuploader.trade.tt:
nslookup ttuploader.trade.tt- The window populates with the full list of currently valid TT IP addresses for file uploads.
File Uploads via Cross-Connects and Private Line
For Cross-connects and extranet "private-line" access into TT platform, a TT representative will work with your networking team to advertise a specific subset of TT allocated IP ranges. These would be provided during the onboarding of the "private-line" via BGP route exchange into your network. The TT platform front-end apps will rely on DNS to leverage the "private-line" paths. Administrators may customize this process as described in the Verifying Access Lines section of the Setup help.